I first heard about this vulnerability a month ago on the Security Now podcast. Fell asleep to a Computerphile episode on it. First discovered by security researchers Simon Aarons and David Buchanan.
Essentially some cropping logic in Pixel phones, Windows snippet tool and possibly others, will crop the images by overwriting part of the existing Portable Network Graphic (PNG) or Joint Photographic Experts Group (JPEG) image, but the rest of the data remains on the file which can then be recovered. Looking at the Portable Network Graphic (PNG) file format details, the beginning of the file starts with an 8-byte "magic number" signature which can be used to determine if the file is indeed a legitimate .png file. After this signature, there will be different chunk types like IHDR, PLTE, IDAT, and IEND. When the file is overwritten all the data starting from the signature to IEND wrote to the same file. When cropping occurs, it's fewer bytes than the original file.
Examining a cropped image that has residual data, you can see the additional data after the IEND footer with a hex-editor:
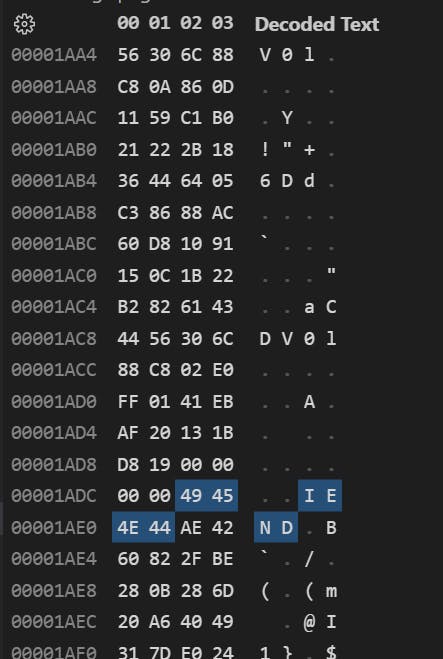
The actual tail of the file:
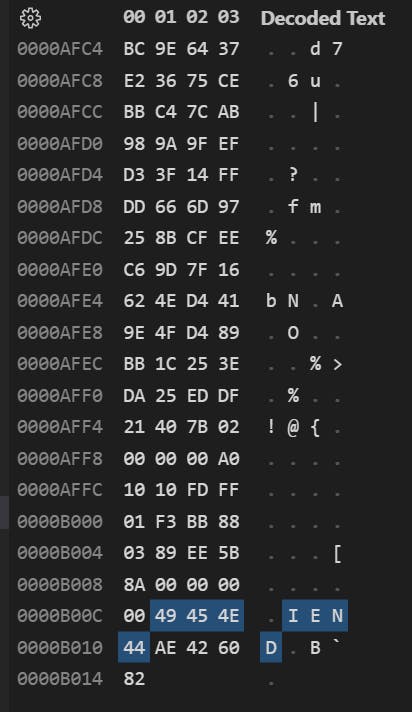
Detection
The acropalypse.app will detect if your images suffer from non-truncated data. However, if you don't feel comfortable uploading your sensitive images to some un-vetted site, you can check out Infobyte's detection and sanitization tool.
I thought it might be fun to see if I could write a simple detection script in Python:
Continuing the fun to see options for detection with Powershell:
The for loop does a byte array comparison for any matching sub-byte array in the read-in file of bytes. The alternative reading in the file as ascii strings then do a comparison to some expected ascii substring for IEND. In theory, you could use regular expressions, but non-ascii characters in the pattern would be problematic.
You can also just do this one-liner for detection.
((Get-Content (Resolve-Path $filename) -Encoding ASCII) -like "*IEND*").Length
Mitigation
You can use Infobyte's detection and sanitization tool or OtiPNG to truncate the residual data for your images.
Learnings
Seems easier to handle byte arrays in Python and the
Countfunction works on byte arrays.You don't need to do a byte by byte comparison if all you want to do is detect. You aren't parsing the chunk types and doing anything with them. For mitigation, you want to detect the
IENDrelevant bytes so you can write everything to a new file.Glad I use
irfanviewto copy sections of a picture and then paste it back to the entire image. The image is then saved to disk or copied once again.The Quite OK Image Format (QOI) is close the compression level of PNG, but its advantage is much fewer computation cycles needed for encoding and decoding. It is also easier to understand the image format than PNG.
