I've been on vacation trying to burn up my PTO and studying. No blogging, just diving deep into Hack-the-Box and security-related topics. I was a bit burned out from Hack Week in July and then a bunch of work stuff before DefCon. On the side, I've been running passive recon scans and found Swagger exposed on an API. At first, I thought it could be that I was on a corporate machine, but I tried on my phone which confirmed it.
An exposed Swagger allows a bad actor to map out your APIs and models even if the accessing of that API requires authentication and authorization.
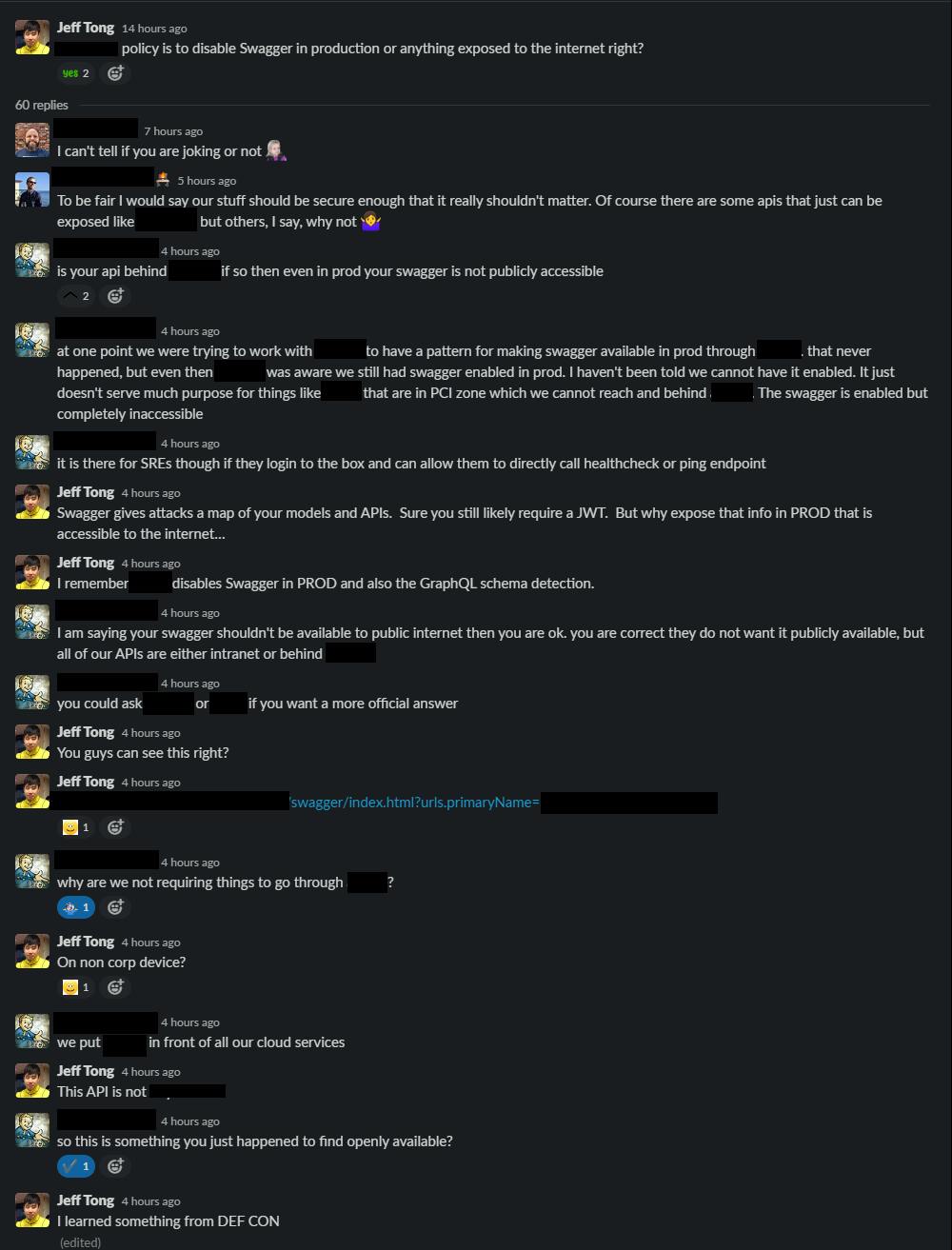
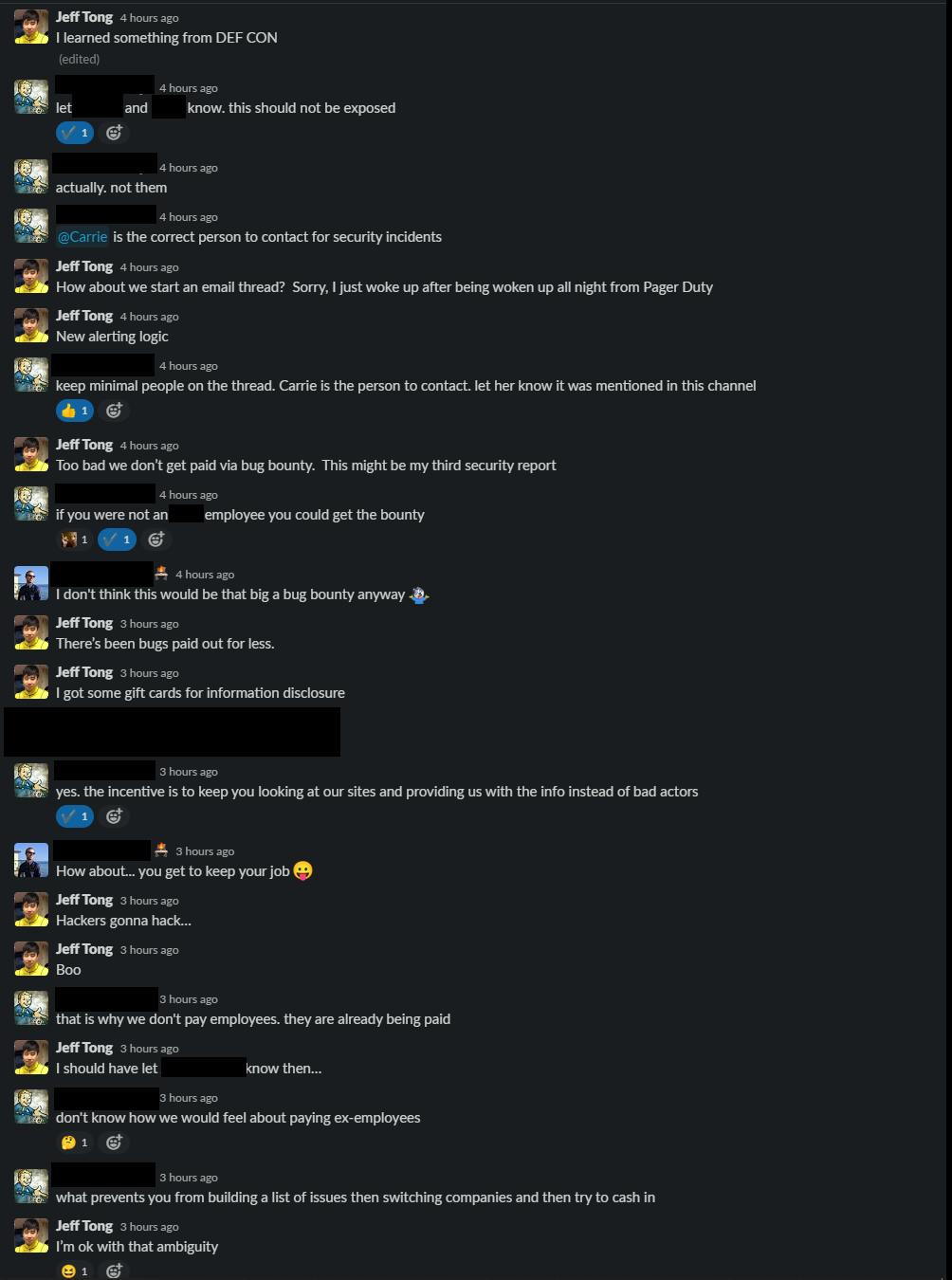
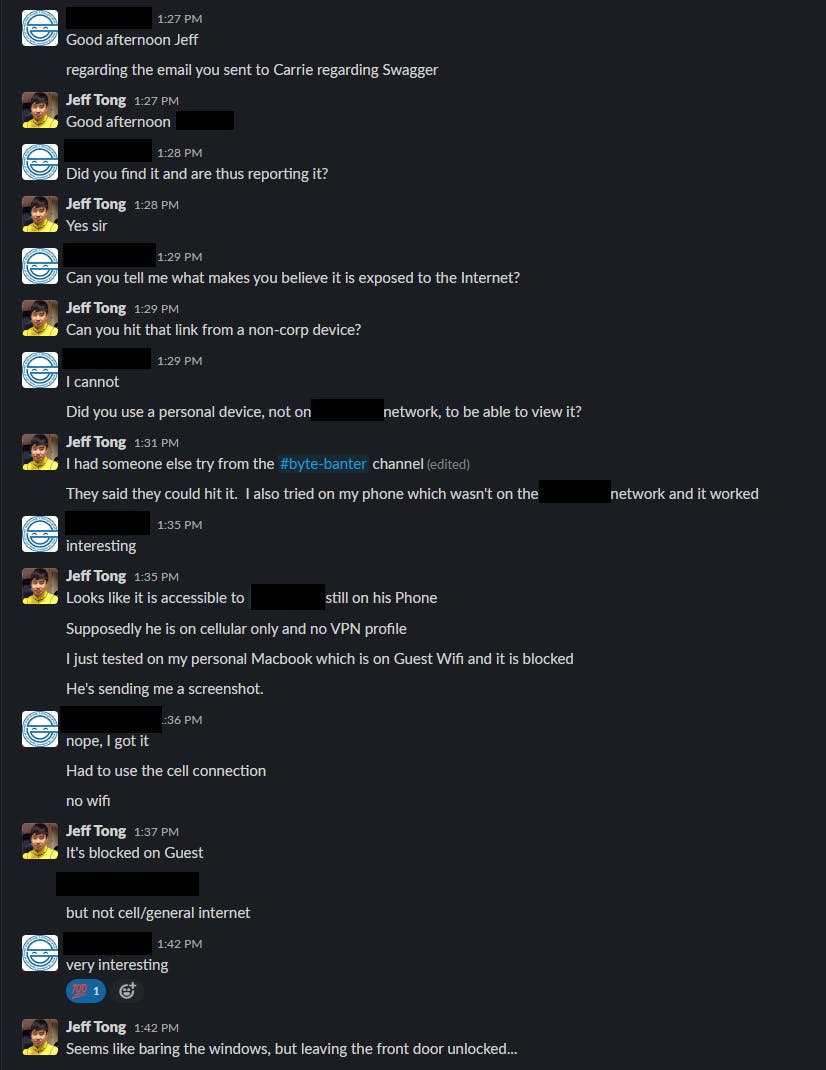
I think this is the third security issue I've reported at the company. The others were related to vendor software with improper authorization and another that was vulnerable to Log4J. It is indeed sad, that I am not ineligible for our Bug Bounty program. Both the non-prod and production Swagger are now disabled.
I learned something at DEF CON.
