Disclaimer: Do not attack networks without permission from proper owners/authorities.
I've been refreshing on the latest WiFi vulnerabilities (PMKID capture) and spending some time with the HAK5 Pineapple Mark VII (BlackFriday deal). I ran across some Deauthentication attack GitHub projects for the ESP8266. A deauth attack is essentially a denial-of-service attack on a WiFi Access Point and connected clients by sending a deauthentication frame to the AP as one of the clients using it's spoofed MAC Address. There is no authentication involved other than this. This allows the attacker to capture the handshakes when the client tries to reconnect as part of the Four-Way Handshake process. Alternatively, the attacker could spoof the targeted AP by denying the clients access in this manner and force them to connect to an evil twin AP.
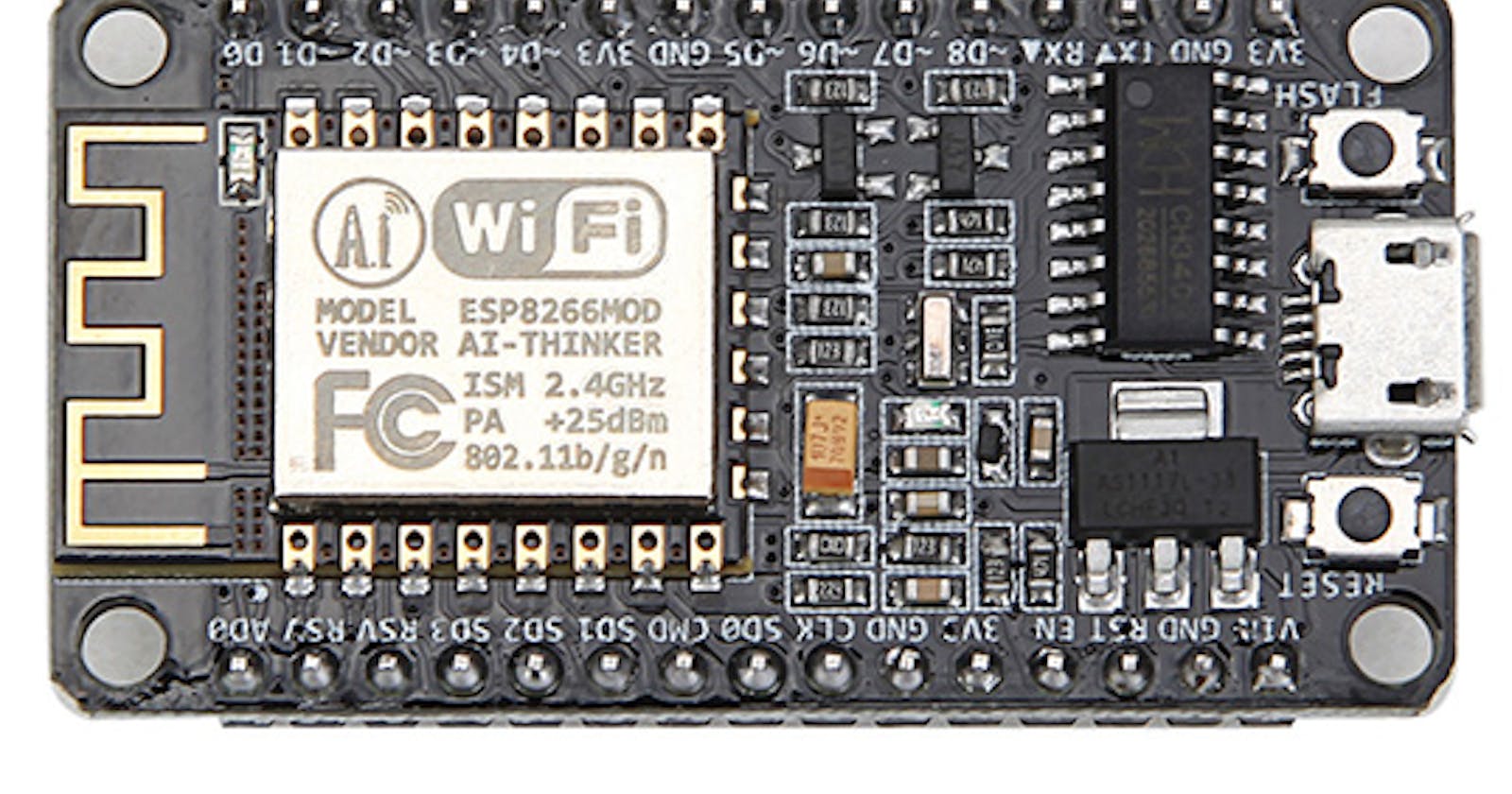
Looking through the Deauther project under the DYI section, I noticed that one of the microprocessors looked like something that I had won at a work raffle once. I thought it was a module for an Arduino and had stashed it away and forgotten about it. This was probably about 5 years ago. Turns out it was an ESP8266 from some off-brand manufacturer.
Following the instructions, it took me about 20 min to get Arduino IDE installed, board package installed, and the memory flashed on the ESP8266. Once flashed, it can be connected through WiFi as the Access Point named pwned and password deauther. The web interface at 192.168.4.1 will let you manage it. There are alternative interfaces also. All the defaults are configurable through the portal.
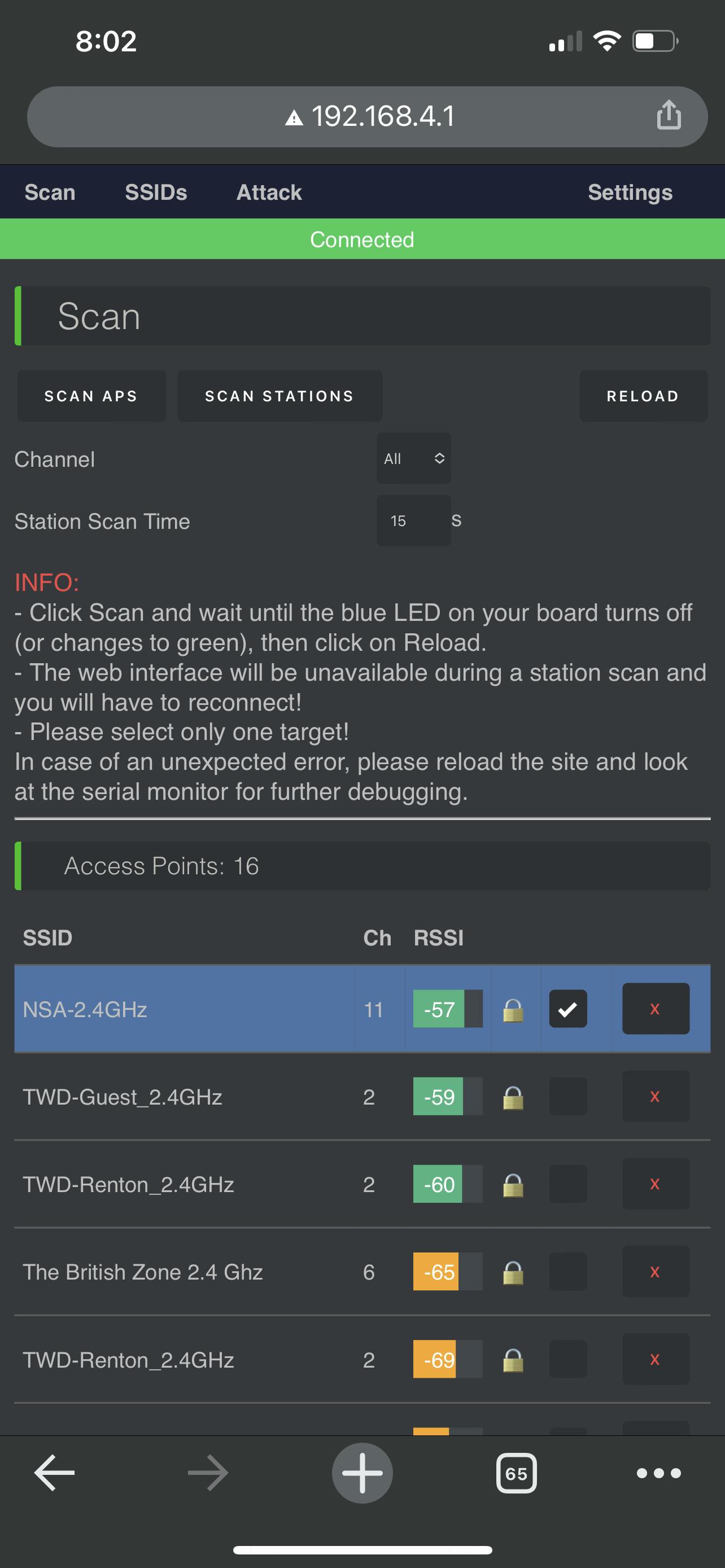
The NSA-2.4GHz is an old D-LINK router that was set up for penetration testing purposes. You have to select an AP and then navigate to the Attack tab.
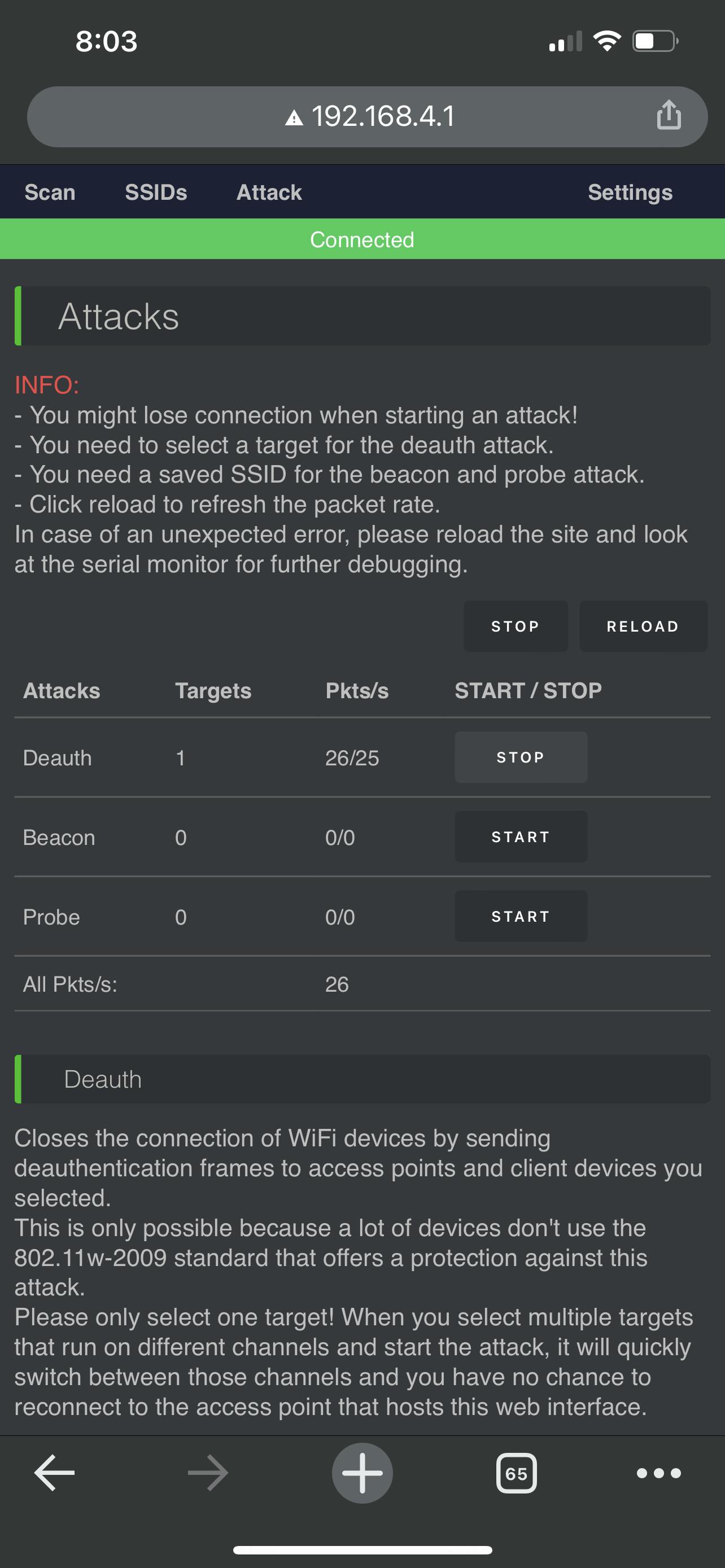
You can see that the network is unable to connect since the attack is set on a timer.
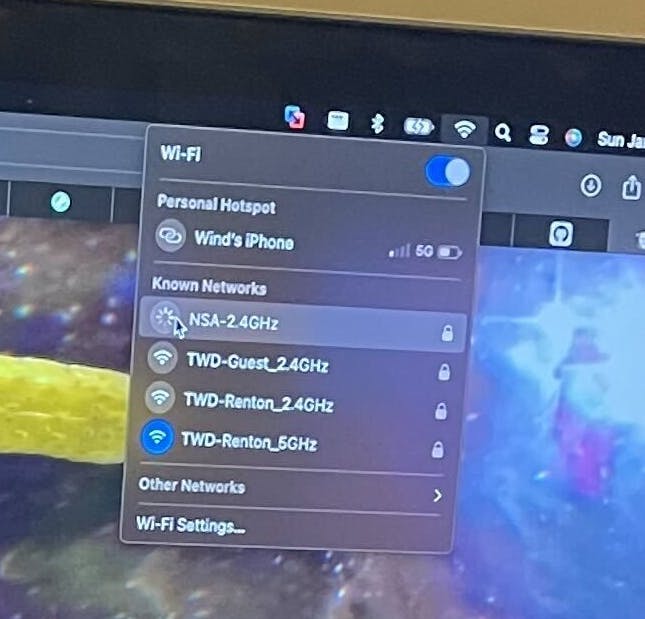

Note that I wasn't able to affect the TWD-Guest_2.4GHz network since this router implements the 802.11w-2009 standard which encrypts the management frame.
Summary
These types of deauth attacks have been done for a while using airodump-ng and others such as JamWifi, but it's cool to see it done on such a small device. Other devices that leverage the ESP8266 exist such as the watch deauther and WiFi Nugget, but it's cool to see the steps and the code to get there.
Note that 5GHz networks are unaffected since this device only operates on the 2.4GHz spectrum, but if you wanted to disrupt that network, use a WiFi adapter that supports monitoring mode and packet injection along with other tools like
wifiteorbettercapor the original aircrack-ng suite.The Deauther project has a captive portal feature, but I didn't play too much with this. Would be cool to try it later and see how well it works.
Use strong passwords for your access point.
Turn off WPS if you don't use it. It can be brute-forced easily. If it was easy before because some router algorithms would not have a timeout for checking the 8-digit PIN and others would validate the first 4 digits before validating the last 3. The last digit is thrown away.
Update your router's firmware or get a modern one that supports higher security standards or OpenWRT if you like to tinker.